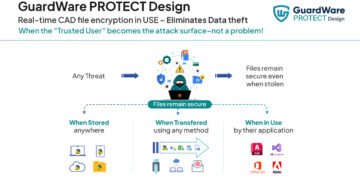
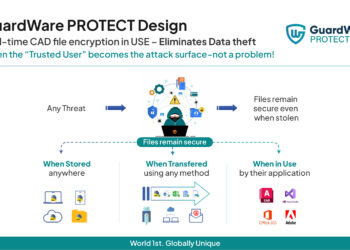
These AI platforms for cybersecurity professionals are transforming the very nature of threat detection and response from a reactive to a predictive discipline. They represent a fundamental shift away from static, signature-based tools towards dynamic systems that learn, adapt, and neutralize threats in real-time. They are the essential tools that allow security experts to scale their capabilities, manage immense volumes of data, and stand a fighting chance against digital threats.
1. Darktrace
Darktrace uses a Self-Learning AI platform known as the Enterprise Immune System that learns the unique digital DNA of an organization’s network.

- Key Features:
- Autonomous Response: Darktrace can take targeted, surgical action to neutralize in-progress attacks, such as ransomware or insider threats, in milliseconds.
- Threat Visualizer: Provides a 3D visual interface that maps the network and highlights anomalous behaviors in real-time, making complex threats easy to understand.
- Unified Coverage: Offers a single platform to protect email, cloud, network, and IoT devices.
- Benefits: By learning what’s normal for your specific environment, it can detect novel threats and zero-day attacks that bypass traditional, signature-based security tools. It reduces investigation time and provides a powerful, automated defense.
2. CrowdStrike Falcon
CrowdStrike Falcon is a cloud-native platform that uses a unified AI model to provide comprehensive endpoint and cloud workload protection.

- Key Features:
- Charlotte AI: An AI assistant that automates complex tasks like threat investigation and response, allowing security analysts to use natural language queries to accelerate their work.
- Indicators of Attack (IOA) Analysis: Goes beyond simple malware signatures to detect malicious behavior and tactics used by attackers in real-time.
- Extended Detection and Response (XDR): Unifies data from endpoints, cloud workloads, and identity to provide a broader view of threats across the entire IT estate.
- Benefits: Its lightweight, cloud-native agent has minimal impact on device performance while providing robust, real-time protection. The platform’s extensive threat intelligence network helps security teams stay ahead of evolving threats.
3. Microsoft Security Copilot
Microsoft Security Copilot is an AI-powered security assistant that integrates with Microsoft’s security products, including Defender, Sentinel, and Intune.
- Key Features:
- Natural Language Queries: Security professionals can use simple language to ask questions, summarize complex incidents, and create KQL (Kusto Query Language) queries for hunting threats.
- Guided Response: Provides step-by-step guidance for incident response, including recommended actions for triage, containment, and remediation.
- Threat Hunting & Vulnerability Management: Can proactively uncover threats that traditional tools miss and identify which devices are missing critical patches.
- Benefits: It significantly accelerates the investigation and response process by automating data gathering, correlation, and contextualization. This makes advanced security tasks more accessible to less experienced team members while freeing up experts for more complex issues.
4. Palo Alto Networks Cortex XSIAM
Palo Alto Networks Cortex XSIAM (Extended Security Intelligence and Automation Management) is an AI-driven platform designed to consolidate multiple security functions into a single system.
- Key Features:
- Unified Platform: Combines the capabilities of SIEM, EDR, SOAR, and threat intelligence into one AI-powered platform, eliminating the need to switch between multiple consoles.
- AI-Driven Incident Prioritization: Automatically connects low-confidence events into high-confidence incidents and prioritizes them based on overall risk, reducing alert fatigue.
- Embedded Automation: Includes hundreds of pre-built automation playbooks and can learn from manual analyst actions to provide recommendations for future automation.
- Benefits: By centralizing data and tools, XSIAM simplifies security operations, accelerates incident remediation, and allows SOC teams to stop threats at scale.
5. SentinelOne Singularity
SentinelOne’s Singularity platform is an autonomous cybersecurity platform that provides comprehensive protection across endpoints, cloud, and identity.

- Key Features:
- Storyline Technology: Patented technology that stitches together every event on an endpoint to create a complete, chronological story of a threat, from start to finish.
- Autonomous Remediation: The platform can autonomously detect, remediate, and even roll back a system to a pre-attack state, providing powerful defense against ransomware and other destructive attacks.
- Singularity Data Lake: Ingests telemetry from both SentinelOne and third-party tools, providing a single repository for threat hunting and investigation.
- Benefits: It offers a hands-off approach to security, providing automated prevention and response without the need for constant human intervention, while its deep visibility helps in detailed forensic analysis.
6. IBM QRadar
IBM QRadar is a powerful SIEM (Security Information and Event Management) platform that leverages AI and machine learning to analyze security data.

- Key Features:
- QRadar Advisor with Watson: An AI-powered component that analyzes and correlates security events to provide detailed insights into attack chains.
- User Behavior Analytics (UBA): Creates a baseline of normal user behavior and detects deviations that could signal a compromised account or insider threat.
- Federated Search: Enables simultaneous querying of data across on-premises and cloud sources without needing to migrate the data.
- Benefits: QRadar helps security analysts manage the high volume of security events by prioritizing the most critical threats and providing the context needed for faster, more informed decisions.
7. Fortinet FortiAI
Fortinet has integrated a deep neural network-based AI engine into its Security Fabric, providing advanced, self-learning threat protection.
- Key Features:
- Virtual Security Analyst: An AI-powered assistant that automates the analysis of complex threats, reducing the time to detect and respond for SOC teams.
- Deep Neural Network (DNN): Trained on millions of clean and malicious files in the FortiGuard Labs, its DNN can identify and classify threats, including sophisticated camouflaged malware, in sub-seconds.
- Autonomous Remediation: Can automatically quarantine attacks by integrating with other Fortinet devices, such as FortiGates.
- Benefits: FortiAI provides a high-speed, autonomous defense against novel threats, making it an ideal tool for short-staffed security teams that need to handle a high volume of traffic and threats.
8. Vectra AI
Vectra AI specializes in Network Detection and Response (NDR), using AI to find and stop threats across hybrid and multi-cloud environments.

- Key Features:
- AI-Driven Attack Signal Intelligence: This technology automates threat detection by analyzing network traffic for attacker tactics and techniques, without relying on signatures or decryption.
- AI-Driven Triage: Prioritizes threats based on their severity and confidence, dramatically reducing the number of detections that require a human analyst’s review.
- Lateral Movement Detection: Excels at detecting a compromised attacker’s movement from one system to another within the network, a crucial stage of most modern attacks.
- Benefits: Vectra AI provides deep network visibility and context, helping security professionals quickly pinpoint and respond to threats that may be hiding in encrypted traffic or blending in with normal activity.
9. Cylance (BlackBerry)
Cylance, now part of BlackBerry, pioneered the use of predictive AI for endpoint security, focusing on threat prevention rather than detection and response.
- Key Features:
- Predictive AI Model: Its AI model inspects files before they can execute, predicting and preventing threats based on their DNA rather than known signatures.
- Offline Protection: The AI model operates directly on the endpoint, allowing it to protect devices even when they are not connected to the internet.
- Minimal System Impact: The lightweight agent uses a fraction of the processing power and memory of traditional antivirus solutions.
- Benefits: By stopping threats at the point of execution, Cylance provides true zero-day prevention. This reduces the need for constant updates and signatures, simplifying security management and minimizing user disruption.
10. Check Point Infinity ThreatCloud AI
Check Point integrates AI into the core of its security platform, with ThreatCloud AI serving as the central nervous system for threat intelligence and prevention.
- Key Features:
- ThreatCloud AI: Aggregates and analyzes big data telemetry from over 150,000 networks and millions of endpoints to provide real-time threat intelligence.
- Over 50 AI Engines: Uses a combination of AI engines to detect and neutralize a wide range of threats, including zero-day malware and phishing attacks.
- Content Disarm and Reconstruction (CDR): A threat extraction capability powered by AI that sanitizes documents in real-time, removing malicious content without disrupting business flow.
- Benefits: This comprehensive and collaborative approach ensures that an organization’s defenses are constantly updated with the latest threat intelligence, providing a prevention-first posture with a near-zero false positive rate.