New Study Reveals a Massive Gap Between Corporate Confidence and the Reality of Always-On Privileged Access
CyberArk has released a startling new report highlighting a critical vulnerability in the age of AI: the Identity-Centric Attack Surface. While organizations are rushing to integrate AI, their security foundations remain dangerously static.
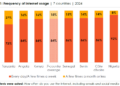
The headline finding is a wake-up call for CISOs: Only 1% of organizations have fully implemented a modern Just-in-Time privileged access model. Despite 76% of firms claiming their strategies are AI-ready, the data suggests a widespread reliance on outdated security assumptions.
The study, which surveyed 500 U.S. practitioners, reveals that always-on access remains the norm, providing a permanent playground for attackers and rogue AI agents.
| Security Metric | Survey Finding |
| Full JIT Adoption | 1% (The Modernization Gap) |
| Always-On Access | 91% have unrestricted, persistent access for 50% of roles |
| AI Access Policies | 33% lack clear policies for AI identity access |
| AI Identity Controls | 45% apply the same controls to AI agents as they do to humans |
The research highlights a growing phenomenon called Shadow Privilege, unmanaged or unnecessary accounts that accumulate silently, often created by automated systems or developers looking for shortcuts.
- Weekly Surprises: 54% of organizations uncover unmanaged privileged accounts or secrets every single week.
- Tool Sprawl: 88% manage two or more identity tools, creating fragmented “blind spots” in the defense architecture.
- The Bypass Factor: 63% of employees admit to bypassing security controls to move faster, while 66% say traditional reviews delay projects.
“Dynamic, evolving environments mean the nature of privileged access, and how to secure it, has fundamentally changed. As AI agents and non-human identities take on increasingly sensitive tasks, applying the right privilege controls to each identity is now essential.” — Matt Cohen, CEO of CyberArk
To survive the AI-driven identity surge, CyberArk recommends a shift from Assumed Trust to Zero Standing Privileges:
- Implement JIT Access: Transition to automated, time-bound access that expires as soon as a task is completed.
- Harmonize Human & Machine Controls: Apply risk-based controls to AI agents and machine identities, recognizing they often have more power than human users.
- Consolidate Identity Platforms: Move away from tool sprawl toward a single, unified identity security platform to eliminate blind spots.
- Adopt Risk-Based Orchestration: Use AI-driven analytics to detect when a privileged action is high-risk and requires extra verification.